Let’s face it; most people tend to use the same passwords over and over, regardless of the application or service they use (both personally and professionally). What’s more, they avoid creating complex passwords for fear of forgetting them. The combination of these two factors is very dangerous, as it makes you very vulnerable. Did you know that it only takes a few seconds to find a password that contains less than 8 characters, even if it contains capital letters, special characters and numbers? This is where multi-factor authentication (MFA) comes in. This is an authentication method that requires at least two verification steps from the user to prove their identity and gain access to their account.
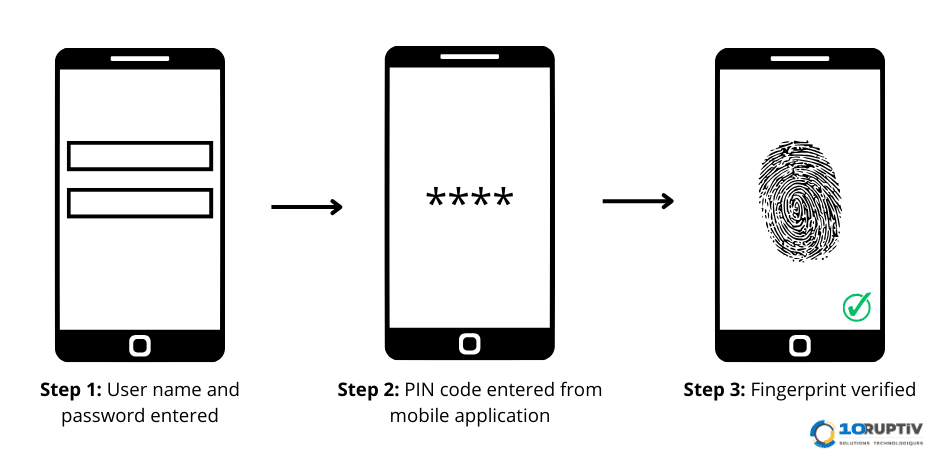
How does it work?
MFA requires additional verification information (factors). One of the most common that users encounter is One-Time Passwords (OTP, which stands for One-Time Password). OTPs are 4- to 8-digit codes that the user receives either by text message, e-mail or via certain mobile applications. These PINS generally expire within 60 seconds (sometimes a little longer).
Multi-factor authentication is based on different types of information, which are classified into 3 categories:
- An element of which the user is aware: such as a code or password;
- An item in the user’s possession, such as a telephone, key or badge;
- An inherent element: a characteristic that is unique to a person, such as his or her voice, face or fingerprints.
Knowledge :
- Answers to personal security questions
- Password
- OTP (OTPs can cover both knowledge and possession, because you know the OTP and you need to have something to get it, like your cell phone)
Possession :
- OTP generated by mobile application
- OTP sent by text message or e-mail
- Access badges, USB keys, smart cards or key rings or security keys
Inherence:
- Fingerprinting, facial recognition, voice, retina or iris analysis
- Other biometric data
However, other types of authentication are being developed with the help of machine learning techniques (a branch of artificial intelligence):
- Location-based authentication: location-based MFA generally checks the user’s IP address and, if possible, geolocation, to ensure that this is the usual location from which the user is trying to connect.
- Adaptive authentication: this authentication mode takes into account the user’s behavior through various factors, such as :
- Where does the user try to access information from?
- When does he try to access information? During or outside working hours?
- What type of device is used? Is it the same as yesterday?
- Is the connection via a private or public network?
It then assigns a risk level to the connection. Depending on the risk level, the user is either immediately authorized to connect, and asked to provide additional information, or is denied access.
And why should we use multi-factor authentication?
Obviously, for security! These days, securing our accounts with just a password isn’t enough. The main aim of MFA is to improve user and corporate security by preventing unauthorized access.
As mentioned in the introduction, using short passwords makes you very vulnerable. Even more so if the user always uses the same password or passwords. A single compromised password can give a hacker easy access to all your online accounts and your personal data.
If you’re worried about forgetting passwords, we recommend using a password manager such as Bitwarden. This tool also allows you to generate very strong passwords, which will be impossible to forget from now on – they’ll be stored in your password vault!

What's the difference between MFA and two-factor authentication (2FA)?
MFA and Two-Factor Authentication (2FA) are often considered to be the same thing. 2FA is actually a subset of MFA, as 2FA restricts the number of factors required to just two, while MFA can require several.
Are there any drawbacks?
While MFA is a great solution for solidifying account security, like everything else, it has a few drawbacks (which we don’t think are important enough to keep MFA out of our lives):
- MFA requires a little more time for each connection, especially if the risk level of the connection is considered high.
- Some authentication modes may require the installation of certain applications, such as an authentication application capable of generating a one-time code, which uses additional space on your device.
- If the user no longer has access to one of the required authentication factors (losing his phone, for example), he may no longer be able to log in. This can take a lot of time and outside help to regain access to the account.
Even if MFA takes a few extra moments and effort to log in, it’s still a very reliable solution for improving account security. Well worth a few extra minutes. 😉


