In a business context, e-mail is king, and popular platforms like Hotmail and Gmail are ubiquitous. However, the method of retrieving e-mails via the POP3 protocol raises challenges that we often overlook. Let’s dive into the security and management issues that come with using POP3 with Hotmail and Gmail, and discover the security, management and compliance drawbacks, exploring the less obvious aspects of these commonly used email services.
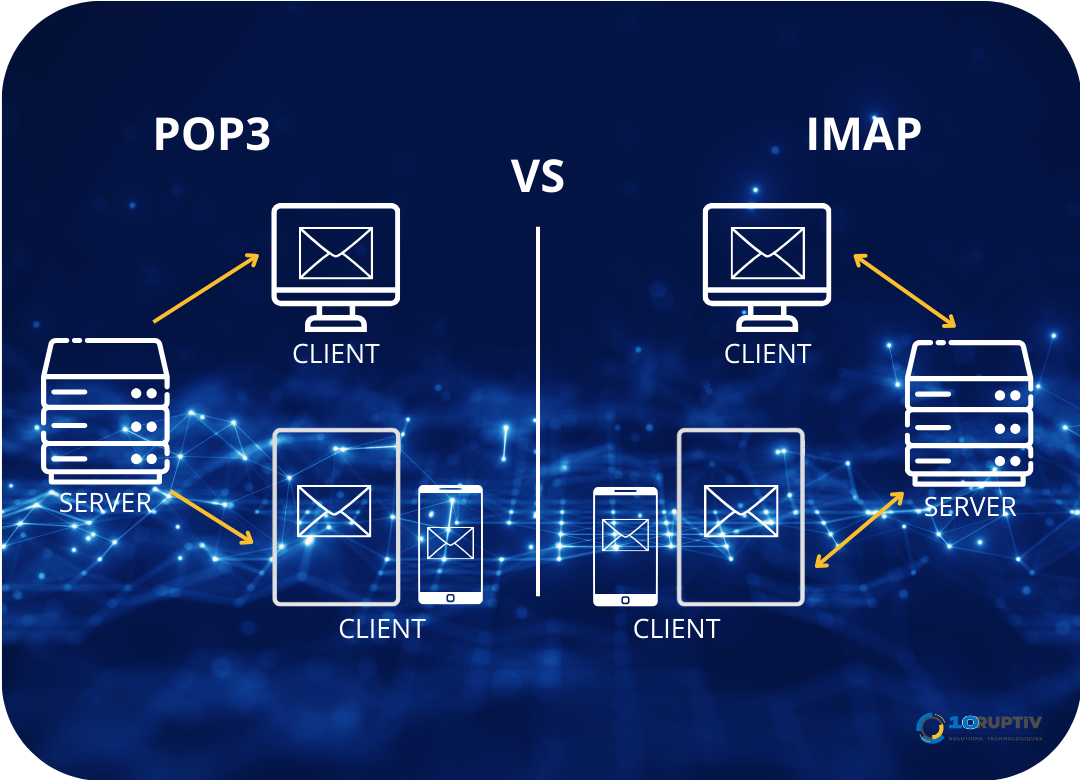
POP3 (Post Office Protocol 3) is a method of receiving e-mail. POP3 is a transmission protocol that allows an individual to retrieve e-mail from a server. It is an older protocol designed for use on a single computer.
POP3 is notorious for its lack of end-to-end encryption. So all data, login credentials and e-mail content is transmitted in clear text, which can be intercepted by malicious hackers. In addition to the lack of encryption, POP downloads e-mails from the server and stores them locally, which could pose risks in the event of theft or loss of devices. Sensitive data can be compromised if appropriate precautions are not taken.
POP3 is also notorious for its lack of synchronization. If a user downloads an e-mail to a different device using the POP protocol, it will appear as a new message instead of indicating that it has been read on another device. Or, if a user has special folders or certain settings defined on one device, if they use POP on another device, they will have to manually create their folders or individually adjust their settings on all devices. In other words, if users organize their e-mail on one device, they’ll have to do it again for every device that uses that POP e-mail account. This can lead to a loss of e-mails if a device is lost or damaged, and obviously the user experience is negatively impacted.

The POP3 protocol is more vulnerable to repudiation attacks. A repudiation attack is when a user denies sending or receiving an e-mail. This can lead to compliance and even legal problems, in certain special cases.
POP’s greatest weakness is undoubtedly its inability to support two-factor authentication (2FA). Account protection is therefore limited to a single factor, which is the password. This makes the account more vulnerable to attacks and unauthorized access if the password is compromised. We invite you to read our article on two-factor authentication to learn more about its benefits, and to make the decision to integrate it into your daily routine.
Today, we mainly use IMAP (Internal Message Access Protocol). Here’s the difference between POP3 and IMAP.
In a professional environment, the use of e-mail addresses such as Hotmail or Gmail can present risks to your company’s security and/or credibility.
Using a generic address (@hotmail, @gmail, @outlook…) for professional communication can give the impression of a lack of professionalism. Customers or suppliers may perceive the company as less established or even less serious. By the same token, this could lead to identity confusion, especially for companies with similar names, which is becoming increasingly common. This could lead to miscommunication and, in the worst case (which is not impossible), reputational problems.
If the company uses a public messaging service, public service means dependence on these providers. If there are problems with the service, or sudden restrictions, this could affect the continuity of communications. What’s more, when using a public service, control over the management of e-mail accounts is limited. The management of users, authorizations and security policies is often more limited than in a customized business domain.
Obviously, there are risks to digital security. Generic e-mail addresses are more often targeted in phishing attacks. Cybercriminals can sometimes exploit the recognition of popular domain names to trick users into accessing their sensitive information. Public e-mail addresses are also often the target of attacks due to their popularity. By using public e-mail services, without a personalized domain, the company could be more vulnerable to phishing and intrusion attempts.
Storing personal data on public e-mail accounts can present risks of data loss due to sometimes less flexible storage policies and potentially less demanding security.
As each industry has distinct standards and regulations, the use of business emails with personalized domains may be required to ensure compliance. So if a company is using a public e-mail service and needs to migrate to a personalized domain (or simply, because it wants to, not simply because it has to) the process can be complex. It could lead to disruptions in communication and account management. A mailbox that doesn’t work is the last thing companies need.


